Exploring the 7 Layers of the OSI Model 🌐
A detailed guide to the “backbone” of computer networking, helping you understand how data travels across the Internet.
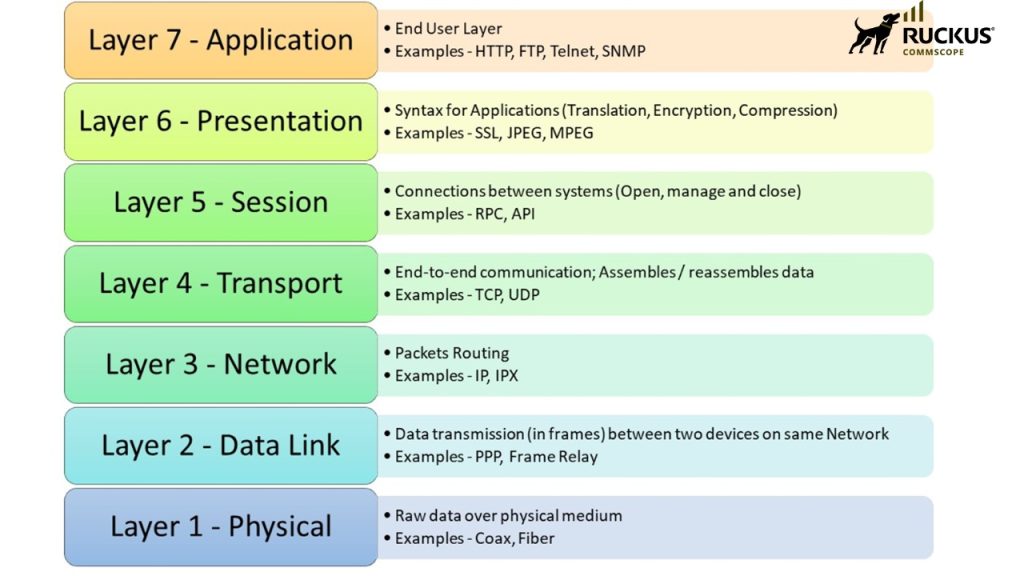
Diagram of the 7 layers of the OSI model
🎬 Layer 7: Application Layer
The User Interface Layer
Function: This is the layer closest to the end-user. It provides network services directly to applications like web browsers, email clients, and file transfer programs. This layer handles user authentication and identifies resource availability.
Common Protocols: HTTP/HTTPS, FTP, SMTP, DNS.
💡 Real-world Example: You open a browser and type “google.com”. The browser uses the HTTPS protocol to send a request to Google’s server and receive the webpage content. This entire interaction happens at the Application Layer.
🎨 Layer 6: Presentation Layer
The Translation Layer
Function: Responsible for “translating” data, encryption, and compression. It ensures that data from the application layer of one system can be read by the application layer of another.
Formats & Protocols: SSL/TLS (for encryption), ASCII, JPEG, PNG, MPEG.
💡 Real-world Example: Before your browser sends your password via HTTPS, the Presentation Layer encrypts it using TLS. When you view a JPEG image, this layer decodes the compressed file into displayable pixels.
🤝 Layer 5: Session Layer
The Dialogue Controller
Function: Opens, manages, and closes “sessions” (connections) between two devices. It controls the conversation, handling synchronization to allow for recovery if a connection is lost.
Common Protocols: NetBIOS, RPC, PPTP.
💡 Real-world Example: When you log into your online bank account, the Session Layer establishes a secure session, keeping your connection active. If you’re inactive, this layer will automatically close the session to protect your account.
📦 Layer 4: Transport Layer
The Reliability Layer
Function: Provides reliable end-to-end data transmission. Its main responsibilities are segmentation (breaking data into smaller pieces), flow control (managing transfer speed), and error control (ensuring data arrives correctly).
Key Protocols: TCP (reliable) and UDP (fast but not guaranteed).
💡 Real-world Example: When you download a large file, TCP at the Transport Layer breaks the file into small segments, numbers them, sends them, waits for acknowledgment, and resends any lost segments. It also manages the download speed so it doesn’t overwhelm your computer.
🗺️ Layer 3: Network Layer
The Routing Layer
Function: Responsible for logical addressing (IP addresses) and routing. It determines the best physical path for the data to reach its destination, moving packets across multiple networks.
Devices & Protocols: Routers, IP (IPv4, IPv6), ICMP.
💡 Real-world Example: An email packet needs to travel from Vietnam to the US. The router in your home forwards the packet to your Internet Service Provider’s (ISP) router. That router, using routing protocols, decides the next “hop” for the packet, and this process repeats until it reaches the final IP address.
🔗 Layer 2: Data Link Layer
The Local Delivery Layer
Function: Responsible for transferring data between nodes on the same local network. It handles physical addressing (MAC address) and encapsulates bits into “frames.”
Devices & Protocols: Switches, Bridges, Network Interface Cards (NICs), Ethernet, Wi-Fi.
💡 Real-world Example: A router has determined a packet needs to be sent to your specific computer on your home Wi-Fi network. The Data Link Layer creates a frame, puts the MAC address of your computer’s Wi-Fi card in the destination field, and sends it out. The switch or Wi-Fi access point ensures that frame is delivered only to your machine.
⚡ Layer 1: Physical Layer
The Hardware Layer
Function: Responsible for transmitting raw data bits (1s and 0s) over a physical medium. It defines electrical and mechanical specifications like voltage levels, cable types, and connectors.
Devices & Standards: Cables (Ethernet, Fiber Optic), Hubs, Repeaters, Modems, Radio Waves.
💡 Real-world Example: This is the most basic level. The 1s and 0s that make up a data frame are converted into electrical signals (for Ethernet cables), light pulses (for fiber optic cables), or radio waves (for Wi-Fi). These signals physically travel through the medium from one device’s network card to another.
Detailed Example: How Does Sending an Email Work?
🚀 Sender’s Side – The Encapsulation Process
Data is gradually “wrapped” through each layer, from top to bottom, to prepare for transmission.
- Layer 7 (Application): You compose an email and hit “Send” in Gmail.
- Layer 6 (Presentation): The email is encrypted (SSL/TLS), and images are compressed.
- Layer 5 (Session): A “session” is opened between your computer and the email server.
- Layer 4 (Transport): The email data is broken into smaller pieces (Segments) and numbered sequentially.
- Layer 3 (Network): Each segment is placed into an “envelope” (Packet) with the sender and receiver IP addresses.
- Layer 2 (Data Link): Each packet is placed into a “shipping box” (Frame) with the MAC addresses of the network card and router.
- Layer 1 (Physical): The entire frame is converted into electrical signals/radio waves/light pulses (Bits) and sent.
📥 Receiver’s Side – The De-encapsulation Process
The process happens in reverse, from bottom to top, to “unwrap” and read the data.
- Layer 1 (Physical): The network card receives signals and converts them back into bits (Frame).
- Layer 2 (Data Link): It checks the MAC address and extracts the Packet from within.
- Layer 3 (Network): It checks the IP address and extracts the Segment from within.
- Layer 4 (Transport): It reassembles all the Segments in the correct order to reconstruct the complete email data.
- Layer 5 (Session): It manages and closes the session once all data is received.
- Layer 6 (Presentation): It decrypts the email and decompresses any images.
- Layer 7 (Application): The final data is sent to the recipient’s Gmail application. Your friend gets a “New Email!” notification.
I envy your work, regards for all the useful articles.